Tactical Wi-Fi interceptor: Extract Intelligence over Wi-Fi
Our tactical Wi-Fi interception solution generates access to the data traffic of your targets’ laptops, tablets, and smart-phones (Android, iOS, Windows Mobile), and silently intercepts the targets’ communications. Our high-tech Wi-Fi spy solution automatically gathers highly valuable intelligence, such as:
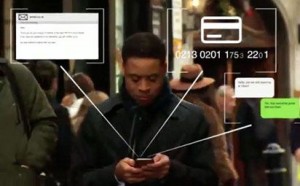
- email messages;
- documents (xls, txt, doc, docx, pdf);
- stored passwords;
- social media passwords and posts;
- live chats history;
- dropbox password and contents;

- phone contact list;
- photo & video files;
- web-browsing activity;
- geo-location data;
- target IMEI number;
- target MAC address.
The router-like box is able to collect all this information automatically from hundreds of mobile devices at the same time. It has a wide geographic reach, meaning that once the box is installed, it can collect data on thousands of people walking by.
Our Wi-Fi spy solution is fully transparent to the target and does not require any cooperation from the phone / laptop owner as long as the target user’s device is nearby and its Wi-Fi transmitter is activated. Going far beyond the interception of off-air traffic, our solution employs innovative active measures to extract secured target data.
The end-to-end Wi-Fi spy solution is built to carry out the entire interception process, from initial access to final analysis. With its tactical design, our Wi-Fi interception solution supports covert operation in crowded areas. The system is tightly integrated and is comprised of a customized hardware with superior operational range (up to 200 meters) and a small case making it a perfect solution for covert intelligence collection operations.
The system requires little technical training. The information collected is presented in a user-friendly graphical interface. Our Wi-Fi interception system was designed with an intelligence operations in mind:
- focus on operational simplicity;
- quick intelligence gathering;
- fast actions and minimal keystrokes;
- maximum automation.
The system consists of two main components:
- A dedicated, durable, all-in-one hardware box that offers extended operating ranges and connectivity in the field. The box fits into many types of backpacks and other portable bags;
- A hybrid laptop that becomes a tablet device with a touchscreen. Field agents use the laptop’s intuitive interface to control the system wirelessly.
With their innocent appearance, the two components are designed to enable operational teams to move around to different locations and deploy the system rapidly and covertly, without attracting attention.
The components communicate wirelessly with each other and operate for hours on internal batteries. Agents can control the box remotely with the laptop from anywhere. Alternatively, the system can be left to work unattended in a car or hideout.
Highlights
- uses active measures to extract data from targets’ accounts and devices;
- gains access to devices by finding the right method for each scenario;
- carries out the entire interception process in a singly end-to-end solution;
- increases operational effectiveness through an intuitive, map-based interface;
- employs several kinds of tools to obtain user credentials and secured data;
- features a tactical design for covert operation in crowded areas;
- offers robust field performance based on proprietary hardware.
SS7 Geolocation & surveillance of any cell phone
SkyTrack is a unique SS7 protocol based solution designed to locate, track, intercept voice calls, SMS and manipulate GSM / 3G / 4G subscribers covertly virtually anywhere in the world, all in real-time using a very friendly user-interface and graphical supported maps, even if the subscriber’s mobile phone is not GPS enabled. SS7 geolocation & surveillance.
Passive GSM Interceptor
The Tactical GSM Interceptor may be used to listen to voice calls, monitor text messages and capture forensic data. All cellular conversations and SMS are recorded on the hard disk of the laptop, allowing evaluation of the intercepted data at any time. View Details.


